A black market hacking tool has the potential to rapidly conduct website scans for SQL injection vulnerabilities at a large scale, all managed from a smartphone through the Telegram messenger.
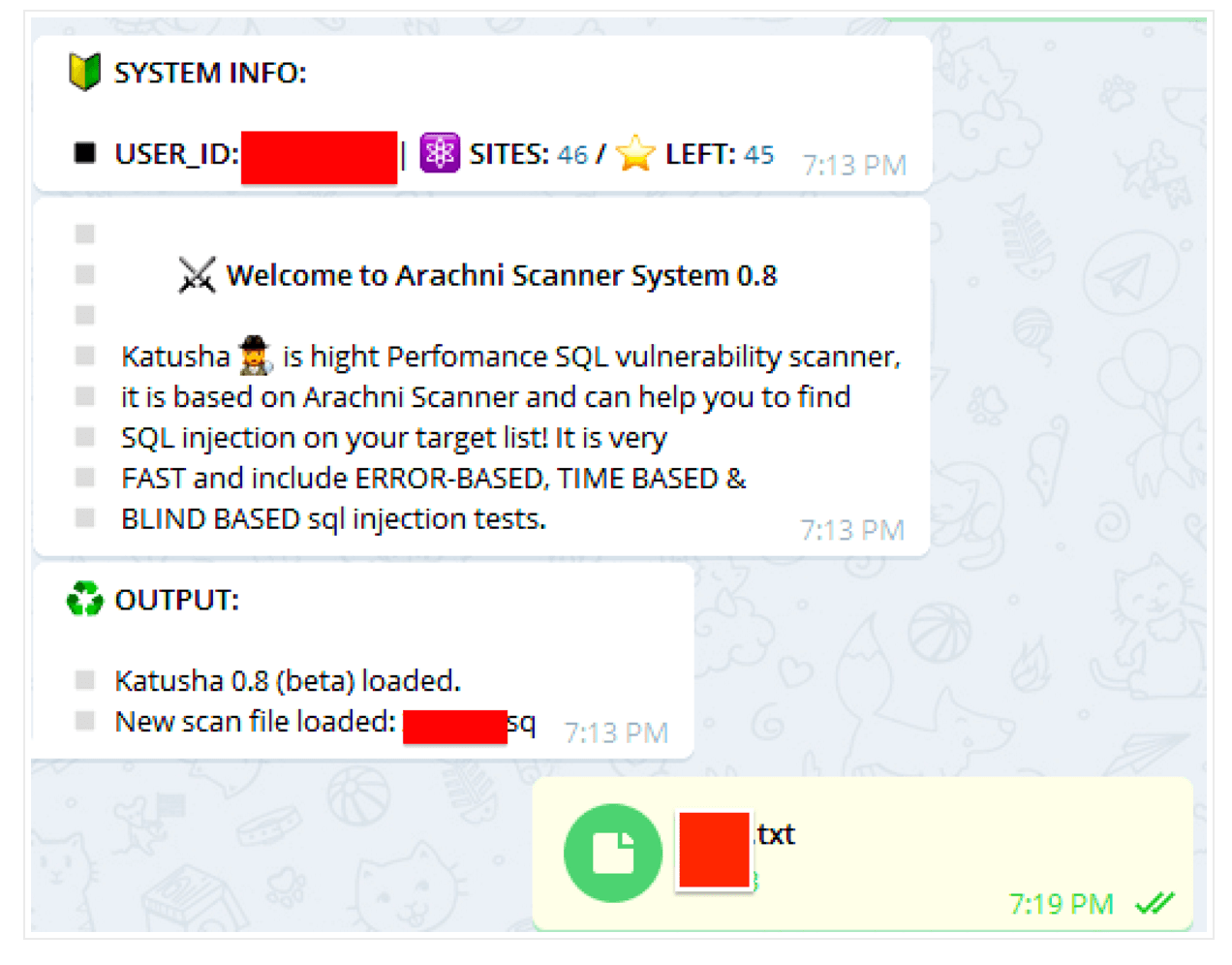
The Katyusha Scanner is a relative newcomer available to black hats that surfaced in early April. It’s a blend of the Arachni Scanner open source penetration testing tool and Telegram; it has already been updated seven times since its introduction, and now Pro and Lite versions are available for between $250 and $500.
Researchers at Recorded Future who found the tool for sale declined to name the site where it’s being offered, and said they have informed law enforcement.
They said the seller is Russian speaking, and that top-tier Russian hackers frequent the forum. The seller is known for selling data stolen from ecommerce websites, Recorded Future director of advanced collection Andrei Barysevich said.
“What we found is a very uncommon tool or service, not offered by criminals before,” Barysevich said.
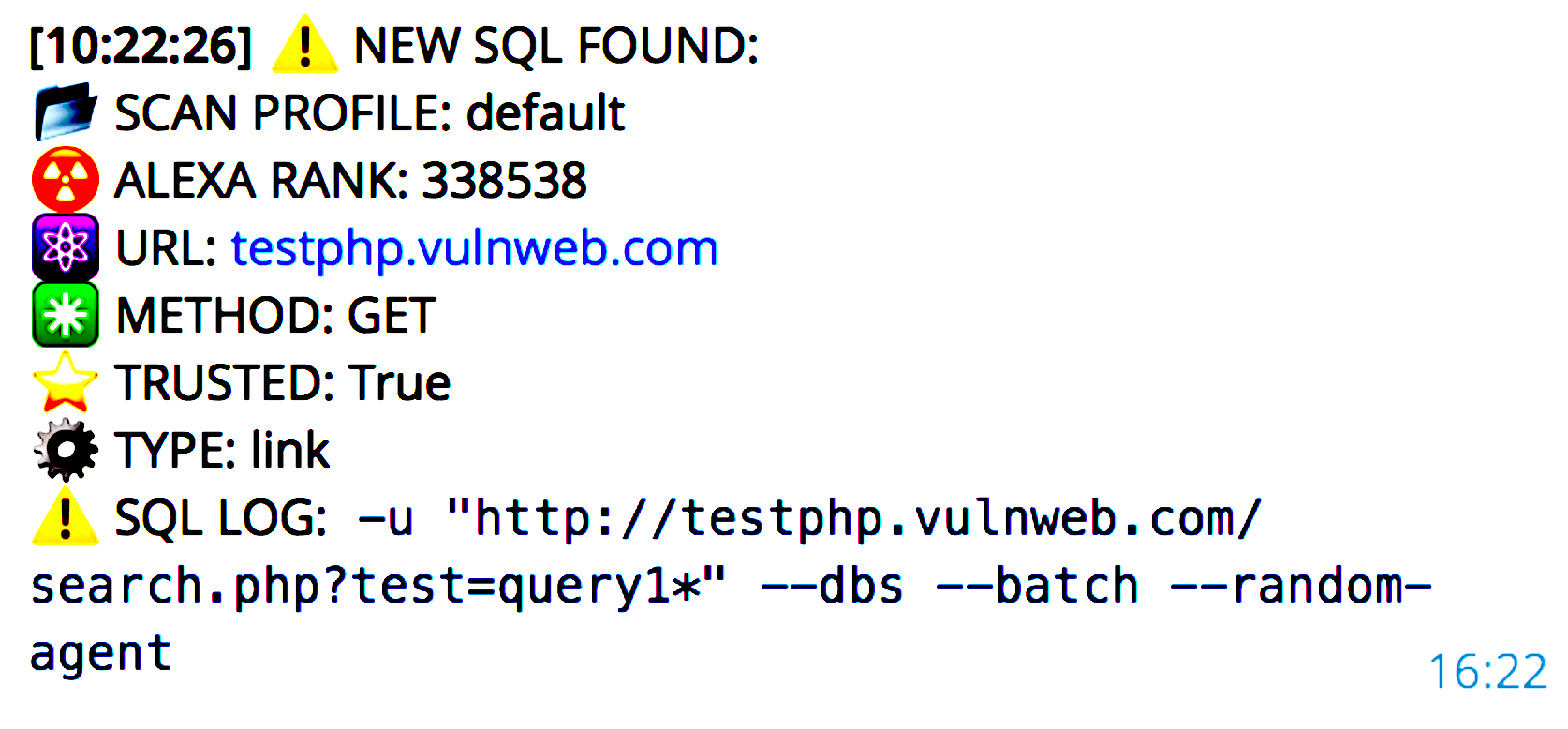
The tool is simple to use, Barysevich said, requiring only that an attacker set up a standard webserver with the version of the Arachni scanner that has been modified so it can be controlled through a linked Telegram account. This allow the scans to be controlled by a mobile device on any platform. Once an attacker has generated a list of websites they want to target—the seller suggests starting with at least 500 sites—it can be uploaded through Telegram and commands can be issued to have it scan the sites for any known vulnerabilities. The Pro version of the tool will then use available exploits to gain a foothold on the system and access data. Once a SQL injection bug is found, for example, the attacker receives a text message with the site name, Alexa rating, and how many databases are available. The tool also has the capability of downloading any exfiltrated data available.
“All of this is done through a simple click on a smartphone,” Barysevich said. “No technical knowledge is required and this is popular now since the price is decent and the return on investment can be significant.”
Barysevich said Recorded Future is aware of 12 to 15 buyers so far, and from alleged testimonials on the black market site, buyers were satisfied with some citing they were able to find as many as eight vulnerable sites after a single scan.
“A massive attack using this tool and these 12 to 15 buyers would be very significant,” Barysevich said. “If you take the number of websites one license can scan on a daily basis and multiply the number these 15 users, we’re talking about thousands of websites being scanned every day if not tens of thousands.
“The speed of the scan is significant, so the potential return and the success rate will be so much higher if the actor starts with a large list of potential victims,” Barysevich said. “By the end of the day he could get 10 vulnerable websites instead of scanning one at a time.”
Barysevich said the potential scale of these attacks is the concern, and that the tool could quickly live up to its name; Katyusha is the name of a World War II-era Soviet rocket launcher that could deliver multiple attacks simultaneously.
“When dozens buy it and initiate attacks every day, the potential fallout will be significant,” he said. “The scale of attacks which is available to criminals is quite unprecedented now. And the convenience of this; someone who wants to engage in this type of activity doesn’t have to be a hacker, he doesn’t have to know how certain tools operate or what exploit packs they should be using. The tool will do everything for them.”
The scanner is still available, and the latest update on June 26 introduced Katyusha 0.8 Pro, which was selling for $500 or available on a $200 monthly license. The light version appeared May 10 for $250 per license.