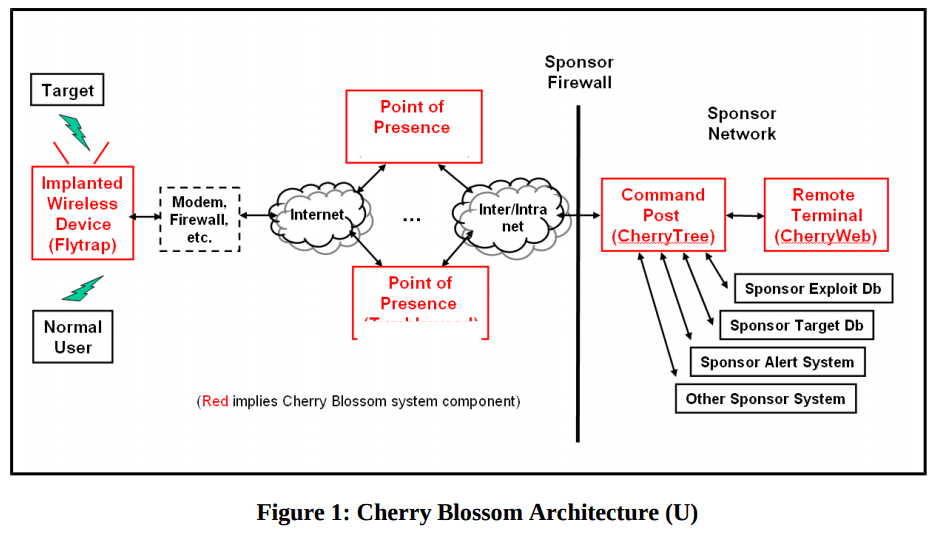
Wikileaks released details of what it claims is a CIA-developed wireless router hacking program targeting home wireless routers and business wireless networks. The program is called Cherry Blossom and leverages custom router firmware called FlyTrap, according to the organization’s latest leak posted Thursday.
“Cherry Blossom provides a means of monitoring the Internet activity of, and performing software exploits on, targets of interest,” according to the report.
The release is part of its ongoing Vault 7 leaks that began in March and have continued almost weekly exposing CIA activities and capabilities.
According to the documents, the CIA created modified router firmware called FlyTrap that could be installed on routers remotely. Once successfully installed, FlyTrap would then monitor the target’s internet traffic and scan for “email addresses, chat usernames, MAC addresses and VoIP numbers.” FlyTrap also allowed government agents to redirect traffic to desirable sites.
“Once the new firmware on the device is flashed, the router or access point will become a so-called FlyTrap. A FlyTrap will beacon over the Internet to a command and control server referred to as the CherryTree. The beaconed information contains device status and security information that the CherryTree logs to a database,” according to Wikileaks.
Listed by the CIA are hundreds of individual consumer- and business-class wireless router models targeted by the agency from brands made by 3Com, D-Link, Linksys and Panet Tec. The Cherry Blossom framework in the alleged CIA documents describes a program and software used for “contract year 2011-2012.”
“If the router is configured to allow firmware to be updated remotely (and tons are) you are at risk. I would put the percentage of (home) routers out there vulnerable to this type of attack at well over 80 percent,” said Rick McElroy, security strategist at Carbon Black.
Exploiting misconfigured routers is nothing new, and something adversaries have been doing for years.
McElroy notes that in March, Wikileaks revealed a similar alleged CIA plot targeting more than 300 enterprise-class Cisco routers and switches. “Based on the ‘Vault 7’ public disclosure, Cisco launched an investigation into the products that could potentially be impacted by these and similar exploits and vulnerabilities,” wrote Cisco at the time in security bulletin announcing fixes for the alleged CIA hacks.
According to Wikileaks documents, FlyTrap is capable of setting up VPN tunnels to Cherry Blossom-controlled VPN servers in order to “give an operator access to clients on the FlyTrap’s WLAN/LAN for further exploitation.”
Clearly the most difficult aspect of a Cherry Blossom program is implanting the FlyTrap firmware on the targeted wireless router. To that end, the alleged CIA document suggests using a CIA exploitation tool such as Tomato or Surfside for targeting vulnerabilities in commercial routers.
In instances where a wireless device doesn’t permit an over-the-air update, the CIA developed what are called “Wireless Upgrade Packages.” It’s unclear what or how these “packages” might be deployed to targeted systems. Also ambiguous, is another suggested means of installing FlyTrap on routers using “the Claymore tool.” According to the leaked CIA document, “the Claymore tool is a survey, collection, and implant tool for wireless (802.11/WiFi) devices.”
The last method for installing FlyTrap on one of the hundreds of routers listed is described: “Use the Device’s Firmware Upgrade Web Page over a Wired (LAN) Link – this technique would likely be used in a supply chain operation,” the alleged CIA describes.
For security expert Udi Yavo, CTO and co-founder of enSilo, he believes this last method mentioned indicates that the CIA intercepted some router devices in the supply chain and created back doors that could later be exploited.
“The CIA has the ability to compromise the device in the supply chain. In these cases, no vulnerability or misconfiguration is needed. However, a lot of IoT devices are easy to compromise. For example, during DEFCON 2016 over 40 zero days were found in IoT devices. And that was in 2016, before that it was even easier,” Yavo said.
“It should be noted, however, that the CBlossom architecture does not limit itself to wireless devices – in general, wired network devices could be implanted/compromised in the same fashion to achieve the same goals,” read the alleged CIA document.